SECURITY, ACCOUNT MAPPING & COMMAND TEMPLATES
SECURITY
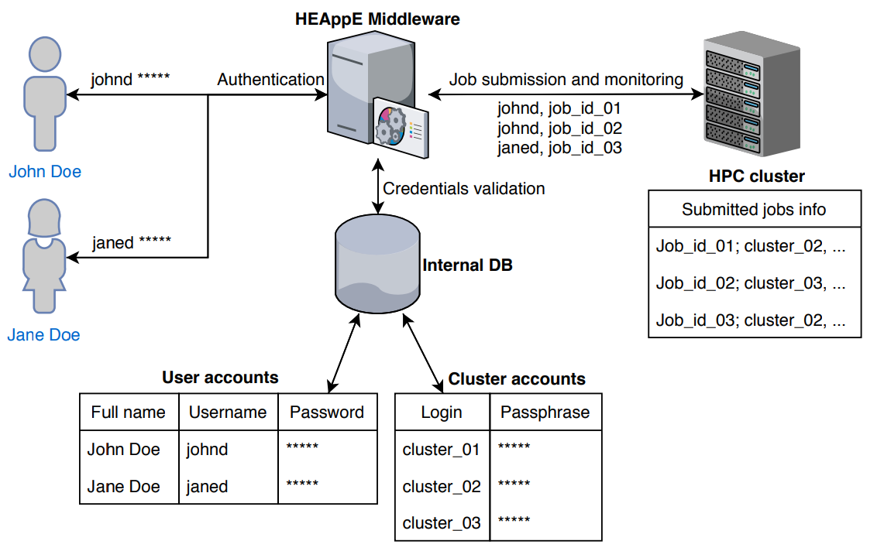
Mapping between an external and internal accounts
- Middleware’s database with the external user accounts and internal cluster accounts
- External user account
- User does not have direct access to the HPC infrastructure
- User authenticates via the Middleware and is able to access only Middleware’s functions
- Internal cluster account
- Cluster account selected from the pool is assigned to each job executed by the user
- Performs the actual job execution
- Cluster account should not leave the HPC infrastructure
Command templates
- User is able to run only a set of pre-prepared job execution templates
SSH Agent as a secure vault for HPC cluster accounts
- Cluster keys managed by the PI of the computational project
Secure data management and data migration between jobs
- Temporary storage for user’s data
- Temporary key used for file upload/download
HEAppE should be deployed within centre´s internal network
ACCOUNT MAPPING
COMMAND TEMPLATES
Command template defines what will be executed on the cluster
- arbitrary script or executable file
- user-defined parameters
- dependencies, third-party software
- queue type for the processing (node type to be used on the cluster)
Wildcards %%{} for the user input parameters
The actual value can be changed by the user for each job submission

Security Audit
-
External security audit performed by

-
Several small to medium issues were found
-
HEAppE’s security was updated mainly to

- Prevent brute force attacks
- Enable rate limitting
- Do not expose unnecessary information
-
Penetration re-test was performed to confirm the fixed issues
